Decrypting the Bitcoin Whitepaper: A Blueprint for Distributed Consensus
Bitcoin's whitepaper theorizes peer-to-peer cash without intermediaries, made possible by a system combining cryptographic verification, distributed consensus and its ingenious proof-of-work.
With our initial exploration into Bitcoin behind us, I find myself drawn further into the rabbit hole that is this pioneering technology. And where better to delve deeper than the very genesis of Bitcoin? Crafted with intricate precision by the elusive Satoshi Nakamoto, the Bitcoin whitepaper is more than just a technical guide; it serves as a blueprint for a revolution that disrupts both the technology and finance industries. Its profound impact has fundamentally transformed our digital technology and financial systems.
Nakamoto—a pseudonym that may represent an individual or a group—began crafting the Bitcoin code in 2007. His efforts culminated on 31 October 2008, when he published a whitepaper titled "Bitcoin: A Peer-to-Peer Electronic Cash System" on the cryptography mailing list at metzdowd.com. This pivotal document introduced the world to Bitcoin.
On 9 January 2009, Nakamoto released the first version (0.1) of the Bitcoin software on SourceForge, and simultaneously, the network came into existence with the mining of the genesis block, which had a reward of 50 bitcoins. What makes this genesis block even more intriguing is the embedded politically charged message in the coinbase transaction: "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks." This statement, referencing a headline from the UK newspaper The Times, serves both as a timestamp and a critique of the perceived instability caused by fractional-reserve banking. This launch marked the beginning of an era, setting the stage for a financial system free from central authority interference.
Nakamoto continued collaborating with other developers on the Bitcoin software until mid-2010. At that point, control of the source code repository and network alert key was transferred to Gavin Andresen, a prominent collaborator in the Bitcoin community. After this transition, Nakamoto withdrew from the project, leaving behind an air of mystery surrounding his true identity. This enigma adds to the intrigue and fascination surrounding the origins of Bitcoin.

Nakamoto's whitepaper introduces us to a unique, decentralized electronic cash system. Bitcoin's innovation shines particularly bright when we consider the unique challenges of the digital realm. Unlike physical transactions, digital ones require safeguards against fraudulent duplication—a phenomenon known as double-spending. Nakamoto ingeniously addresses this issue with a proof-of-work consensus model, enabling secure, trustless transactions that are free from central oversight and interference. This groundbreaking system allows for independent transactions liberated from the surveillance of centralized authorities.
In this essay, we're building upon our foundational understanding of Bitcoin to dissect the deeper, more intricate aspects of the Bitcoin whitepaper. We'll be focusing not just on the sophisticated mechanisms that drive Bitcoin but also on the wider implications and transformative potential encapsulated in Nakamoto's vision. We'll explore the intricate concepts, delve into the technology underpinning Bitcoin, and speculate on the future possibilities that emanate from the pages of the Bitcoin whitepaper. The objective is to further illuminate Bitcoin's significant impact within the evolving intersections of technology and finance, empowering our readers with a deeper, more nuanced understanding of this pioneering digital asset.
So, let's dive in, crack open that whitepaper, and uncover the hidden layers of this digital revolution.
Companion Essays
This is the second essay in a series introducing Bitcoin to Humanist Activists. The other essays in the series are available here.
The Abstract
The Bitcoin whitepaper's abstract succinctly encapsulates the central premise: to engineer a purely peer-to-peer form of electronic cash facilitating online payments directly from one entity to another, bypassing the need for a financial institution. It underscores the role of digital signatures in resolving the double-spending issue, pointing out the redundancy of a trusted third party and its accompanying drawbacks.
The rest of the document elaborates on these points with greater technical depth, expanding upon the key points presented in the abstract. The paper delves into the intricacies of achieving a peer-to-peer electronic cash system through Bitcoin, covering cryptographic principles, distributed network design, and incentive structures.
The whitepaper tackles the issue of double-spending and presents how Bitcoin overcomes it through a decentralized network. Transactions are validated through consensus among nodes, and the collaborative efforts of these nodes maintain a shared ledger, commonly referred to as the blockchain in contemporary terminology, which records all transactions. The paper further explains the security measures employed in the ledger through cryptographic hashes and proof-of-work implementation.
In essence, the abstract's core points receive comprehensive elaboration in the whitepaper, providing a detailed exposition of Bitcoin's workings and its potential ramifications in finance and technology. The full paper delves deeply into the technical intricacies, fulfilling the purpose outlined succinctly in the abstract.
The Introduction
The introduction of the Bitcoin whitepaper eloquently addresses a significant flaw in the traditional payment system, which heavily relies on financial institutions as trusted intermediaries for electronic transactions. It articulately highlights the inherent weaknesses of this system. For instance, the costs associated with mediation—such as transaction fees charged by banks and credit card companies, expenses related to dispute resolutions, and overheads linked to account maintenance—limit the feasibility of small, everyday transactions, not just large ones. The dependence on trust in this traditional system also increases the risks of fraud and identity theft. Furthermore, it underscores a broader societal cost: the forfeited ability to execute non-reversible payments for non-reversible services, opening up merchants to risks associated with chargebacks.
In response to this problem, the whitepaper puts forth a groundbreaking solution based on cryptographic proof, effectively eliminating the need for trust or intermediaries. It proposes a system that enables direct transactions between any two willing parties without requiring a trusted third party. The persuasive presentation of the system's advantages, including seller protection against fraud and the convenience of implementing routine escrow mechanisms for buyer protection, further bolsters the case for Bitcoin's superiority over the existing paradigm.
The author effectively sets the stage for the subsequent sections by illustrating the relevance and significance of Bitcoin as a transformative solution to the tangible challenges plaguing the current electronic payment system. The author convincingly portrays Bitcoin as a superior alternative to the existing paradigm through persuasive tactics and language.
Transactions
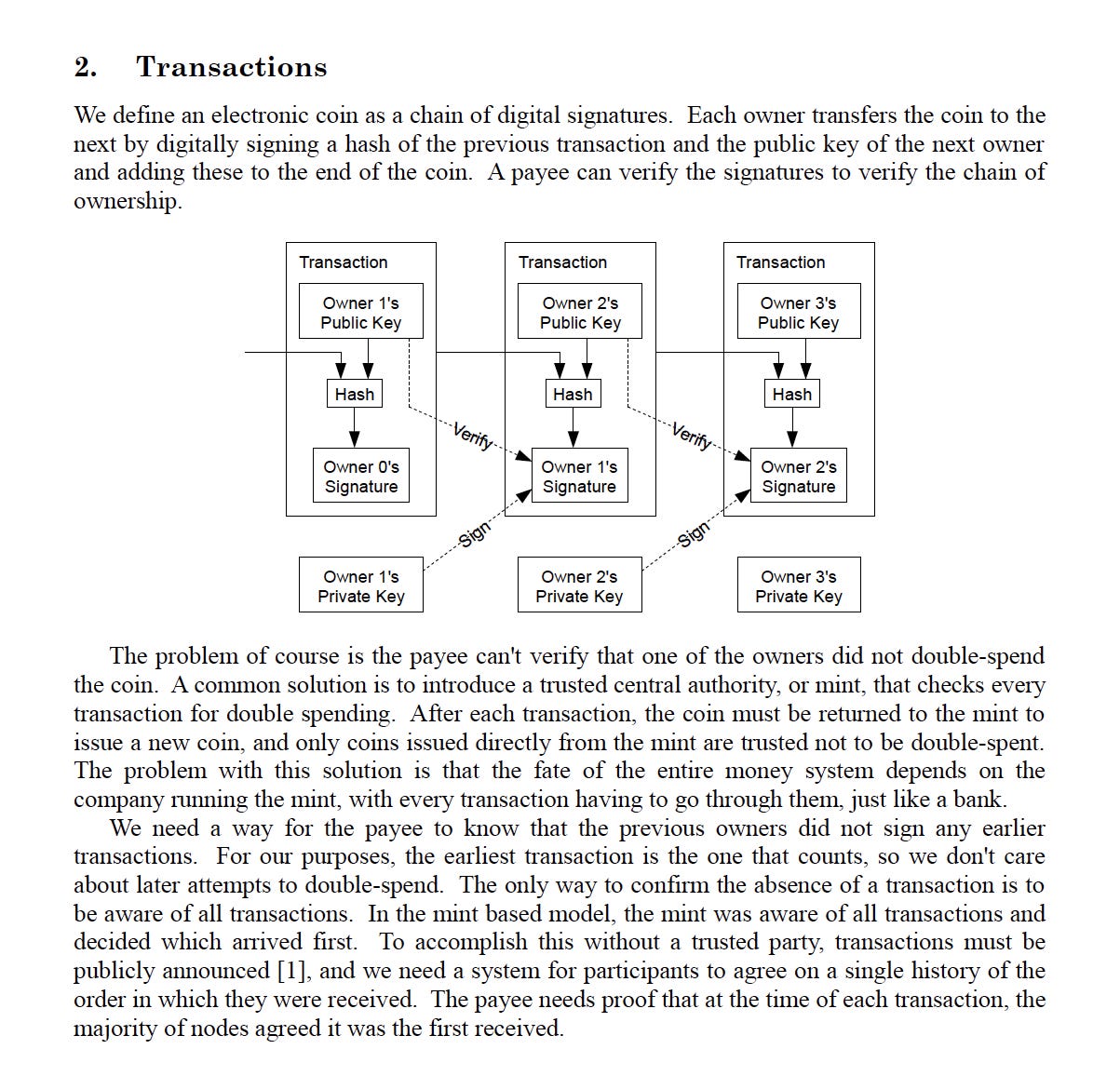
Section 2 of the Bitcoin whitepaper provides an in-depth examination of how Bitcoin transactions operate. At the core of this system is the representation of coins as chains of digital signatures. In this context, a digital signature is a cryptographic tool that provides proof of ownership. Each coin owner transfers the coin by signing a hash—a unique digital fingerprint—of the previous transaction and the public key, a cryptographic code that allows the receiver of the coin to access it, of the new owner. This process generates a chain of signatures, creating a verifiable transaction history essential for maintaining the integrity of the system and preventing fraud.
Once transactions are initiated, they are broadcast to the network, where they undergo a validation process by network nodes. This section of the whitepaper expands on this process, explaining how these validated transactions are then grouped into blocks. Miners, participants who validate and record transactions into the blockchain, combine these blocks and add them to the blockchain, a public ledger of all transactions. Additionally, it further discusses the role of transaction fees as incentives for miners to include transactions in the blocks they mine, ensuring the total number of bitcoins in circulation never exceeds a predetermined limit.
Building on this transaction framework, the whitepaper proposes a robust and secure system that employs cryptographic proof, removing the need for trusted intermediaries—a key feature of traditional financial systems. By making transactions computationally difficult to reverse, a level of irreversibility is attained, which is a unique selling point for Bitcoin. The system also allows for the integration of routine escrow mechanisms and contractual agreements where a third party holds and regulates payment to protect buyers during transactions.
Building on the system's reliance on cryptographic proofs, a notable feature of Bitcoin is its resilience against attacks by malicious nodes. This resilience relies on an important assumption: that honest nodes dedicate more computational resources (CPU power) to maintaining the blockchain than any cooperative group of malicious nodes. This power dynamic is crucial to maintaining the security of the system.
However, the whitepaper does acknowledge potential limitations and vulnerabilities. If this assumption fails - that is, if dishonest nodes somehow accumulate more computational power - the system would be susceptible to attacks. Furthermore, while the system aims for transaction irreversibility, the whitepaper acknowledges that absolute irreversibility may not be achievable.
Section 2 of the Bitcoin whitepaper presents a comprehensive analysis of the system, acknowledging its potential vulnerabilities while emphasizing its benefits. It underscores the importance of a trustless and decentralized system, achieved through cryptographic techniques, to ensure security, eliminate the need for trusted intermediaries, and prevent double-spending.
While the whitepaper recognizes that absolute irreversibility may not be attainable, it proposes the use of routine escrow mechanisms to protect buyers during transactions. These mechanisms serve as a safeguard against fraud and provide an additional layer of security within the system.
Importantly, the whitepaper does not suggest the involvement of financial institutions in dispute resolution scenarios, which is required to maintain decentralization and avoid introducing trusted intermediaries. Instead, it highlights the benefits of a decentralized system that operates without the need for a centralized authority, allowing participants to transact directly with one another.
In comparison to traditional financial systems, the Bitcoin system offers distinct advantages. It enables smaller and casual transactions—those of low value or infrequent nature—that would be impractical within conventional systems due to fees or bureaucracy. It also allows for non-reversible payments in exchange for non-reversible services. However, the transparency of public transaction announcements limits the privacy attainable when compared to conventional banking models.
This section provides comprehensive technical details on Bitcoin transactions, including their validation and processing within the network. While highlighting the system's resilience and fraud resistance through cryptographic proof, the author also acknowledges the limitations, such as the dependency on the assumption that honest nodes control more CPU power and the fact that absolute irreversibility may not be achievable, both inherent in the system's design.
Timestamp Server
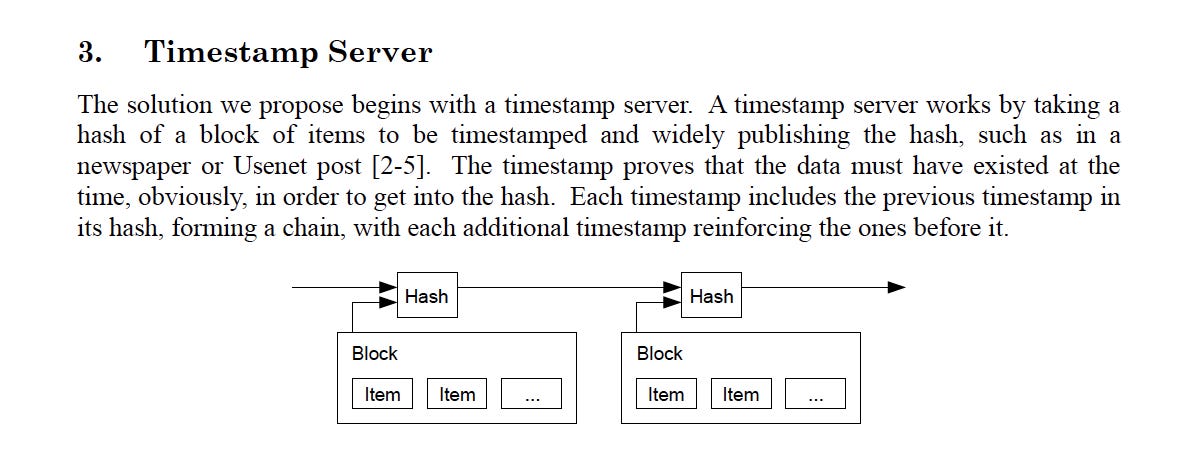
The 3rd section explores the importance of a timestamp server in preventing double-spending. It replaces the traditional reliance on trusted third parties for transaction monitoring with a decentralized timestamp server that establishes the chronological order of transactions.
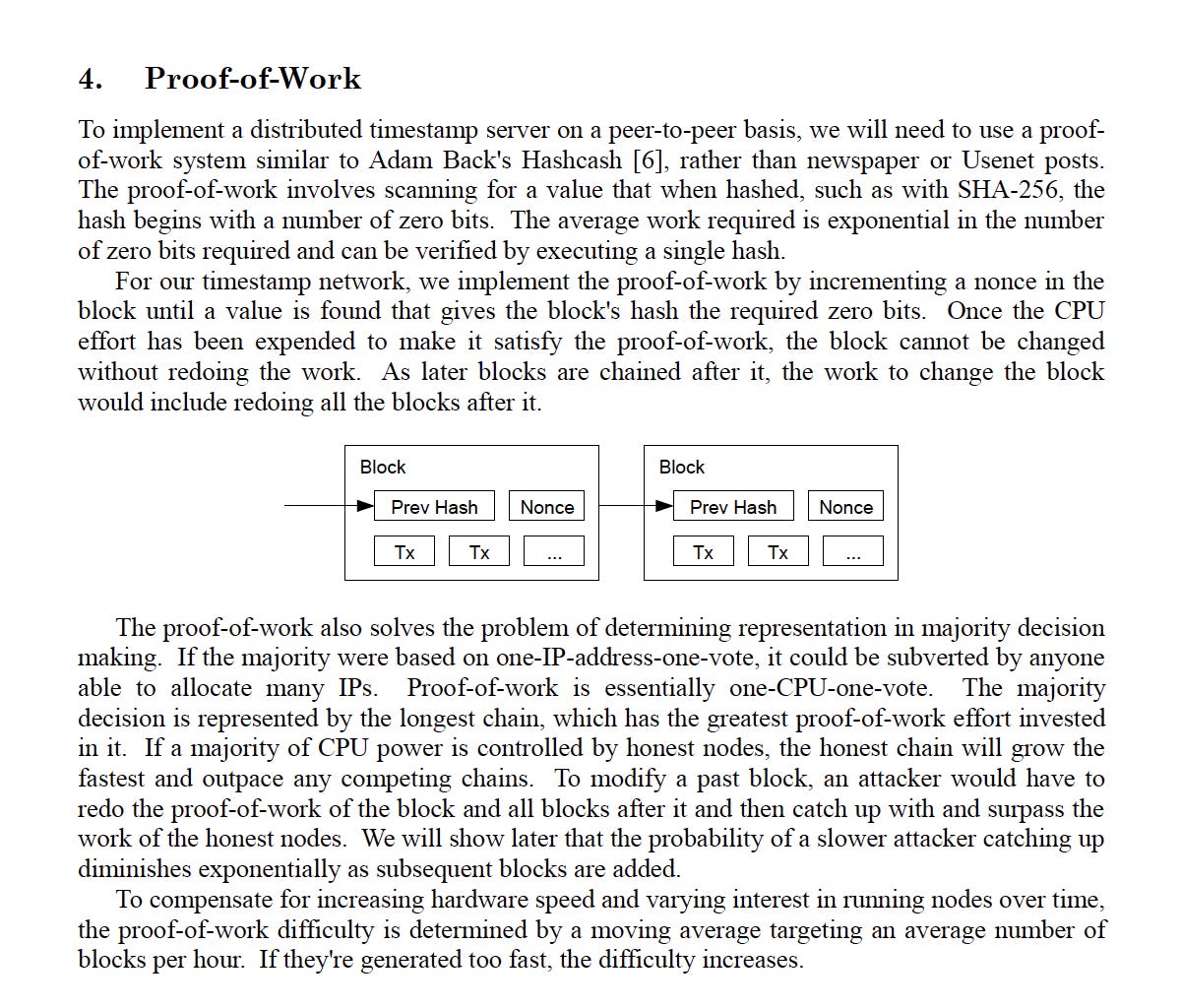
The timestamp server plays a crucial role in Bitcoin's double-spending solution. The timestamp server functions by taking the hash of a block of transactions and incorporating it into the subsequent block's hash. This creates a chain of blocks, known as the blockchain, which is resistant to alterations unless the proof-of-work for all subsequent blocks is redone. By hashing each block with the previous block's hash, an immutable and tamper-proof chain is formed.
Within the network, nodes validate the blockchain by adhering to the protocol that the longest chain is the correct one. This mechanism ensures the integrity of the system and defends against potential network attacks.
The timestamp server plays a crucial role in Bitcoin's double-spending solution. It timestamps a set of items by hashing them and widely publishing the hash. Each timestamp includes the previous one, creating a reinforcing chain that serves as irrefutable evidence of the data's existence at a specific time.
The blockchain, which incorporates the timestamp server, consists of blocks that contain the hash of the previous block, a timestamp, and transaction data. Altering the chain would require redoing the proof-of-work for all subsequent blocks, rendering it computationally impractical.
The system's effectiveness in preventing double-spending relies on the assumption that honest nodes control the majority of CPU power, as the longest chain is considered the valid one. This design makes reversing past transactions computationally infeasible, as it would require recalculating the proof-of-work for all subsequent blocks.
However, the system's effectiveness is contingent on the assumption that the majority of CPU power is controlled by honest nodes. If this assumption fails, the system could become vulnerable to attacks. Specifically, the paper is referring to what is now known as a 51% attack, where a malicious entity gains control of the majority of the network's computing power.
By integrating the timestamp server and blockchain, the Bitcoin system provides a robust solution to the double-spending problem. It ensures the integrity of transactions and the chronological order of events, eliminating the need for a trusted third party and enabling secure peer-to-peer transactions.
In essence, this section clarifies the mechanisms by which the timestamp server operates within the Bitcoin network, highlighting its significance in preventing double-spending and fortifying the security and reliability of the system.
Insight Nugget:
Have you ever wondered about the terminology surrounding the technology introduced in the Bitcoin whitepaper? Although the original paper does not mention the terms "blockchain" or "timechain," they have become integral to our discussions on this groundbreaking innovation.
The term "blockchain" has gained widespread recognition as the popular name for the technology described in the whitepaper. It represents a decentralized, immutable ledger composed of interconnected blocks, each containing transaction data and referencing the previous block; thus, the more commonly used word "Blockchain" aptly captures the essence of the system's structural design.
Interestingly, Bitcoin maximalists have also coined the term "timechain" to describe the same underlying concept. This term emphasizes the chronological ordering of transactions within the system. By referring to it as the "timechain," they highlight the fundamental characteristic that distinguishes Bitcoin's ledger from traditional databases.
Similarly, while the Bitcoin whitepaper does not explicitly mention the term "51% attack," it has become the common terminology used to describe the vulnerability of the Bitcoin network when a malicious entity gains control of the majority of the network's computing power.
While Nakamoto did not use these specific terms, the concepts they represent align with the innovative ideas presented. The emergence of words like 'blockchain' and 'timechain' within the Bitcoin community reflects the collective effort to find convenient and descriptive labels for this groundbreaking technology. It highlights the dynamic nature of language and terminology in response to technological advancements and the ongoing quest to articulate and communicate complex concepts.
Proof-of-Work
Next, we dive into a comprehensive exploration of the Proof-of-Work (PoW) consensus mechanism, a cornerstone of the Bitcoin network. Recognized as a key groundbreaking innovation by ardent Bitcoiners, PoW serves as a formidable shield against spam and denial-of-service attacks, leveraging computational challenges to safeguard the network's integrity.
PoW mandates a substantial computational effort prior to the addition of a new block to the blockchain, demanding undeniable proof of computational work. Miners must discover a hash that fulfills specific criteria, necessitating significant computational resources. The inherent complexity of this challenge acts as a deterrent against the inundation of invalid blocks.
The whitepaper explains that adjustable PoW difficulty ensures a steady rhythm of block creation. In this mechanism, miners are motivated to contribute their computational resources to the network by receiving newly minted bitcoins as a reward for discovering valid blocks. The paper addresses potential network attacks and unveils the corresponding defensive measures.
Within Bitcoin's PoW system, miners diligently search for a value that begins with a certain number of zero bits when hashed (such as with SHA-256). The effort required to pinpoint such a value exponentially escalates with the increasing zero bit threshold, while its validity can be swiftly ascertained through a single hash operation. PoW difficulty remains agile, adjusted by a moving average that seeks to maintain a specific average block production rate. If blocks are generated too quickly, the difficulty is adjusted to maintain the desired pace.
Despite its effectiveness, the PoW system has faced criticism for the substantial computational power and consequent significant energy consumption required to solve the cryptographic puzzles, raising concerns about carbon emissions.
The PoW system has attracted scrutiny from those concerned about the environment. However, Bitcoiners assert that such concerns are often misguided. It is important to clarify that Bitcoin itself, or the mining machines involved, does not produce energy or emit carbon into the atmosphere. Instead, Bitcoin operates as a consumer, much like electric vehicles, washing machines, or dryers. Proof of Work actively seeks out the most cost-effective form of energy and typically relies on regulated energy sources. Therefore, environmental concerns should primarily be directed towards the point of energy generation rather than the point of consumption. Bitcoiners firmly believe that the energy consumption associated with PoW is justified by Bitcoin's unparalleled value proposition, dismissing criticisms raised by skeptics.
In light of these environmental concerns, alternative consensus mechanisms like proof-of-stake have emerged as potential remedies. In a proof-of-stake system, validators assume block creation responsibilities based on their cryptocurrency holdings rather than computational resources. However, Bitcoiners firmly reject this approach. See the below insert for elaboration.
However, PoW does encounter its own set of hurdles, particularly regarding scalability. As the Bitcoin network grows and transaction volumes increase, there is a corresponding increase in the demand for computational resources to solve cryptographic puzzles. This can result in longer transaction times and higher transaction fees. The pursuit of scalability has spurred further innovation within the Bitcoin developer community, with ongoing efforts to enhance layer 1 efficiency, explore Layer 2 technologies like the Lightning Network, and improve the overall performance and scalability of the Bitcoin network. Further exploration of the subject is beyond the scope of this analysis.
The Battle of Consensus
Individuals who are new to Bitcoin or have not fully grasped its value proposition often advocate for a misguided shift towards a proof-of-stake (PoS) system due to questionable environmental concerns. However, for Bitcoiners who uphold a deep commitment to the principles of decentralization, immutability, and security, preserving the robustness of the Proof-of-Work mechanism remains an essential component of the network's inherent value.
Bitcoiners firmly believe that PoW is indispensable and merits unwavering support and defence. They assert that PoW is the only consensus mechanism that has been rigorously tested and proven to function effectively at scale, providing the necessary security foundations for the Bitcoin network. Moreover, they contend that PoW is the sole means by which decentralization can be preserved, preventing any single entity from gaining control over the network.
Critically, Bitcoiners contend that adopting proof-of-stake (PoS), the proposed alternative consensus mechanism frequently advocated by critics of Bitcoin lacks the same level of security as proof-of-work (PoW) and is susceptible to centralization. They argue that PoS is inherently less secure than PoW and continues to perpetuate the flaws of the existing systems that Bitcoin aims to rectify but is now automated on a blockchain. Through auditable chain data, Bitcoiners substantiate their claims, revealing that PoS disproportionately favours those with the largest coin holdings, thereby fostering a concentration of power and compromising the very essence of decentralization.
Network
The Bitcoin network operates as a decentralized, peer-to-peer entity. Its infrastructure facilitates the seamless communication of transaction and block information among nodes, ensuring the free exchange of data. This open and inclusive nature allows nodes to enter or exit the network at will, bolstering its resilience against attacks and system failures.
Within the network, nodes play a crucial role in authenticating transactions and blocks using digital signatures and the blockchain. This process serves as a safeguard against double-spending, ensuring that each transaction is exclusive to a single block. The Bitcoin network fortifies its defences and deters potential network attacks by incorporating these authentication mechanisms.
At its core, the Bitcoin network provides robust protection against fraud for sellers, thanks to its careful engineering to counteract malicious activities from nodes. Transactions carried out on the network are computationally impractical to reverse, which assures high security. This robust protection also facilitates the straightforward implementation of regular escrow mechanisms to protect buyers.
However, it is important to acknowledge that the Bitcoin network is not impervious to vulnerabilities and potential attacks. The most significant threat is the possibility of the previously mentioned 51% attack, which occurs when a group of nodes gains control over more than half of the network's total computational power. In such a scenario, these malicious nodes could manipulate the blockchain, reversing transactions or even double-spending coins.
Despite these challenges, the Bitcoin system continually evolves and improves its defences. Implementations such as Segregated Witness (SegWit) and the Lightning Network have significantly enhanced the network's scalability and transaction speed.
SegWit achieves this by implementing transaction batching, which involves segregating transaction data from signature data. This segregation reduces transaction sizes, allowing for more transactions to be processed in each block. By optimizing the use of block space, SegWit enhances scalability and increases the overall efficiency of the Bitcoin network. Additionally, the Lightning Network introduces the concept of off-chain transactions, enabling the execution of transactions outside the main blockchain. This approach alleviates congestion on the blockchain, leading to faster transaction speeds and improved scalability.
Looking ahead, the Bitcoin community stays committed to enhancing network security and resilience through continuous innovations within the existing proof-of-work (PoW) mechanism. This steadfast commitment to the principles of decentralization, immutability, and security excludes the consideration of alternative consensus mechanisms like proof-of-stake.
Furthermore, Bitcoiners emphasize the importance of incorporating additional security measures to mitigate risks and protect against fraud or theft. One such measure is the implementation of multi-signature transactions, which require multiple signatures to validate a transaction, thereby reducing the risk of unauthorized access or manipulation. By embracing these additional security measures, the Bitcoin network further strengthens its defences and ensures the integrity of transactions.
While acknowledging the existence of potential vulnerabilities, it is crucial to recognize that the Bitcoin network is meticulously designed to defend against attacks from malicious nodes. Its continuous development and implementation of improvements underscore its unwavering commitment to enhancing the network's robustness, security, and scalability. These ongoing efforts, rooted in the battle-tested and proven PoW consensus mechanism, further strengthen the network's antifragility over time.
Incentive
Here Satoshi lays out the details of the incentive structure that motivates miners in the Bitcoin network. This structure crucially maintains the integrity and security of the blockchain.
Miners and service providers in the Bitcoin network can earn newly mined bitcoins through their active participation. The mining reward, also known as the Coinbase reward, a fundamental component of the incentive system, gradually diminishes over time to ensure that the total number of bitcoins in circulation remains within a predetermined limit. The creation of new coins in each block serves as a powerful incentive for miners, akin to gold mining, where resources are expended to add gold to circulation. Bitcoin miners contribute to the network's operation by expending CPU time and electricity while receiving rewards for their efforts.
In addition to mining rewards, transaction fees play a vital role in the incentive structure of Bitcoin. When the output value of a transaction is less than the input value, the difference becomes a transaction fee, which is added to the incentive value of the block containing the transaction. As the circulation of bitcoins increases, transaction fees have the potential to become the primary source of incentives, creating a system that is resistant to inflationary pressures. The Bitcoin community recognizes the importance of this ongoing development and actively engages in discussions to explore potential solutions for the future sustainability of the network once all coins have been mined. These discussions reflect the community's commitment to ensuring the long-term viability and continued success of Bitcoin as it evolves to meet the changing needs and challenges of the digital economy.
The design of Bitcoin's incentive structure is intentional; it aligns miners' interests with the network's overall security and integrity. It ensures that even if a potential attacker possesses more computational power than all the honest nodes combined, it remains more profitable for them to follow the rules rather than undermine the system and invalidate their own wealth.
However, concerns surrounding the long-term sustainability of the incentive structure have been raised. As the coin supply increases, mining rewards per block decrease, potentially resulting in a decline in the number of miners and posing a potential risk to the network's security. To mitigate this, Bitcoin incorporates a built-in mechanism that adjusts mining difficulty based on the total computational power of the network, guaranteeing a constant block creation rate even as mining rewards diminish.
Although Bitcoin's incentive structure maintains fairness by motivating miners to adhere to the rules and contribute new blocks, the network also acknowledges the need to actively address and adapt to long-term sustainability concerns. This commitment to continuous improvement demonstrates the Bitcoin community's dedication to the network's long-term success and resilience.
Coinbase Transaction
The Coinbase transaction holds a significant role within the Bitcoin ecosystem. As an integral part of the cryptocurrency network, it serves as the initial transaction in a newly mined block, rewarding the dedicated miner with freshly minted coins.
Unlike regular transactions that involve the transfer of existing coins, the Coinbase transaction creates brand new coins and assigns them to the miner's address. By incorporating this transaction in each block, Bitcoin incentivizes miners to contribute their computational power to uphold the blockchain's integrity and security.
The term "Coinbase" derives from the merging of "coin" and "base," symbolizing the creation of new coins as the foundation of each block. While not explicitly mentioned in the whitepaper, the concept of the Coinbase transaction underscores the innovative nature of Bitcoin.
In Bitcoin, the Coinbase transaction holds additional significance with the inclusion of a special feature known as the coinbase script. This script allows miners to embed short messages or extra data within the transaction. It was through this feature that Satoshi embedded the now-famous "chancellor on the brink" message in the Genesis block.
By enabling the creation of new coins and motivating miners to participate actively, the Coinbase transaction serves as a fundamental building block of the Bitcoin network. Its existence highlights the interplay between transaction processing and coin generation, ensuring the system's integrity and security.
Notably, the popular cryptocurrency exchange Coinbase draws its name from the foundational concept of the Coinbase transaction in Bitcoin, paying homage to the visionary work of Satoshi Nakamoto.
Reclaiming Disk Space
This section details how the Bitcoin network manages the storage of old transactions. As the blockchain continues to grow with the addition of new blocks, it can impose significant data storage requirements. To address this challenge, the Bitcoin network has implemented a mechanism to discard spent transactions once buried sufficiently under subsequent blocks, effectively reclaiming valuable disk space.
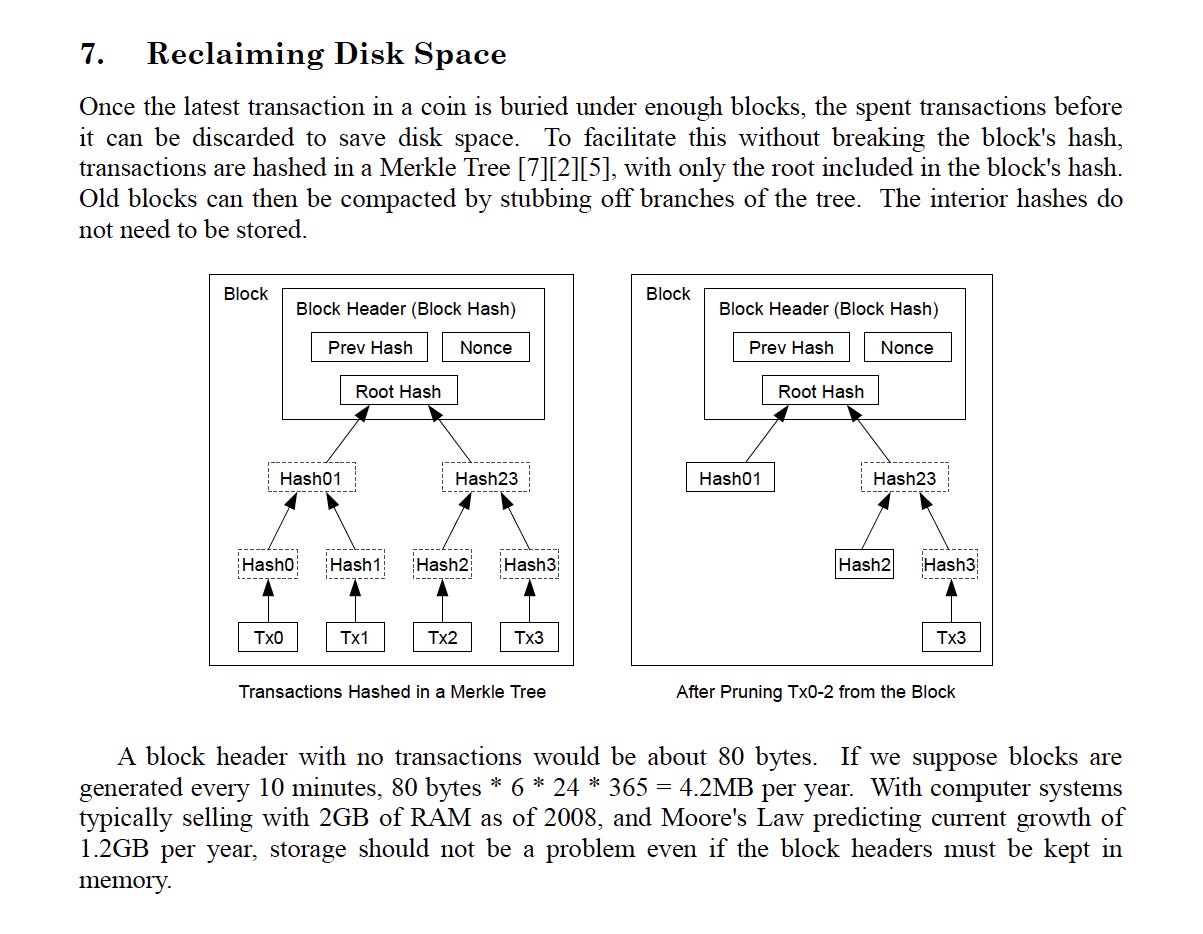
This process uses a Merkle Tree structure, enabling the discarding of spent transactions without compromising the integrity of the block's hash. By hashing the individual transactions and incorporating only the root hash into the block's hash, the network ensures that the block remains secure while optimizing storage efficiency.
The ability to reclaim disk space by discarding old transactions is of utmost importance for the overall efficiency of the Bitcoin network. It alleviates the storage burden on nodes, particularly those with limited capacity such as mobile devices or low-end hardware, as they only need to retain the most recent transactions.
However, it's important to address certain considerations associated with this feature. When a node discards old transactions, there is a possibility of limited verification capabilities for all transactions in the blockchain. To mitigate any potential security vulnerabilities, the Bitcoin community has introduced a technique called "pruning." Pruning allows nodes to selectively discard older transactions while retaining the ability to verify the validity of all transactions.
The Bitcoin network is continuously evolving with various developments aimed at optimizing storage efficiency. Notable advancements include the Taro upgrade, which encompasses improvements to the Bitcoin protocol. The upgrade introduces features such as Schnorr signatures, Taproot, and Merkelized Abstract Syntax Trees (MASTs), enabling more efficient and flexible transactions and smart contracts on Bitcoin.
Furthermore, the Bitcoin network benefits from the ESS scheme. This efficient storage scheme leverages the distribution characteristics of unspent transaction outputs (UTXOs). The scheme dynamically prunes blocks with lower query frequency, enhancing scalability and reducing storage requirements. It also facilitates instant verification of most transaction inputs, reducing communication costs.
Furthermore, the Lightning Network, a second-layer solution built on top of the Bitcoin network, plays a significant role in improving storage efficiency. By utilizing payment channels, the Lightning Network enables fast and cost-effective transactions without the need to broadcast every transaction to the main chain. This approach saves storage space and reduces fees while enhancing privacy and scalability.
These ongoing advancements, including the Taro upgrade, the ESS scheme, and the Lightning Network, underline the community's commitment to optimizing the network's efficacy, scalability, and security.
Key Technical Terms Explained
In discussing the Bitcoin network's storage efficiency, several technical terms have been mentioned that may be unfamiliar to non-technical readers. Let's briefly explain these terms to expand the reach of our analysis:
- Merkle Tree structure: A Merkle Tree is a data structure used in Bitcoin to efficiently verify the integrity and inclusion of transactions within a block. It hashes individual transactions, combines them into pairs, and hashes those pairs until a single root hash, known as the Merkle root, is obtained. This structure allows the network to discard spent transactions without compromising the integrity of the block's hash, optimizing storage while maintaining the ability to validate transactions.
- Pruning: Pruning is a technique that allows nodes in the Bitcoin network to selectively discard old transactions while retaining the ability to verify the validity of all transactions. It helps reduce storage requirements by removing unnecessary transaction data, making the network more efficient.
- Schnorr signatures: Schnorr signatures are a cryptographic signature scheme used in Bitcoin to verify the authenticity of transactions. They offer several advantages, such as the ability to combine multiple signatures into a single one, which improves efficiency and enhances privacy.
- Taproot: Taproot is an upgrade to Bitcoin that enhances privacy and scalability. It introduces a new scripting language that enables more complex and flexible transactions while reducing their visibility on the blockchain, thereby improving privacy..
- MASTs (Merkelized Abstract Syntax Trees): MAST is a technology that allows for more space-efficient and flexible smart contracts on the Bitcoin network. It organizes the conditions and clauses of a smart contract using a Merkle Tree, reducing the storage requirements while still maintaining the ability to enforce the contract's rules.
- UTXOs (Unspent Transaction Outputs): UTXOs represent the outputs of Bitcoin transactions that haven't been spent. Each UTXO contains an amount of Bitcoin and the information needed to spend it. They are crucial for validating transactions and ensuring the integrity of the blockchain.
Understanding these technical terms gives us a broader perspective on the innovations and technologies employed in the Bitcoin network to optimize storage efficiency and improve its overall functionality.
Simplified Payment Verification
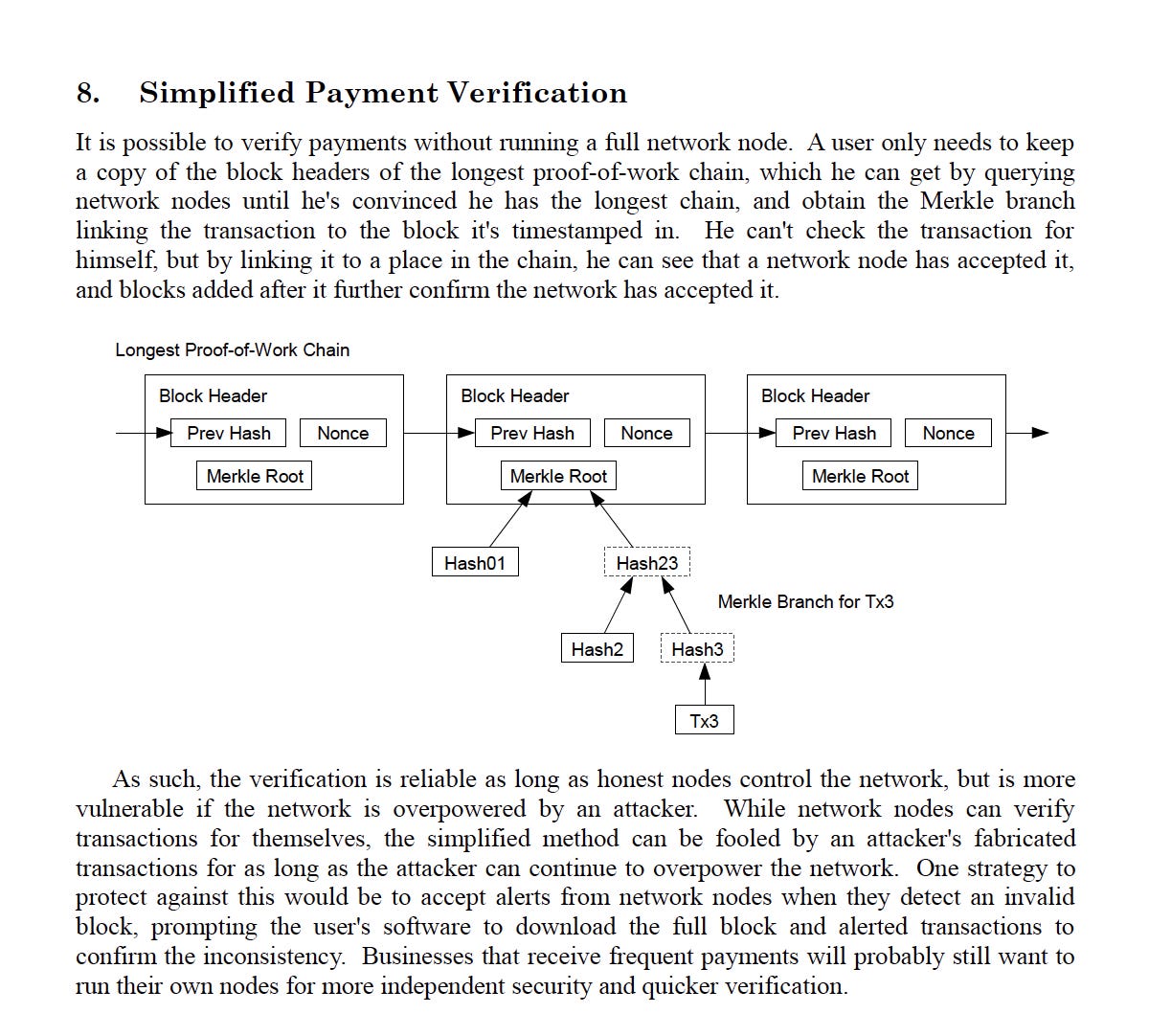
This section explores Simplified Payment Verification (SPV), a form of light client described by Satoshi Nakamoto in the Bitcoin white paper. SPV allows lightweight nodes to authenticate transactions without the need to download the entire blockchain, making it particularly useful for nodes with limited resources, such as mobile devices.
Instead of burdening themselves with storing the entirety of the blockchain, SPV nodes opt to maintain solely the block headers of the longest proof-of-work chain. These block headers, significantly smaller in size compared to full blocks, contain essential information such as the hash of the previous block header, the Merkle root of the transactions within the block, and other relevant metadata. By focusing on these concise block headers, SPV nodes effectively reduce their storage requirements while still retaining essential data for transaction verification.
The utilization of block headers by SPV nodes offers distinct advantages. These headers serve as condensed summaries of the corresponding blocks, providing key information necessary for establishing the validity and integrity of transactions. By including the hash of the previous block header, SPV nodes can trace the sequential nature of blocks, forming a secure and tamper-proof chain. The Merkle root, contained within the block header, ensures the verifiability of transaction inclusion within the block, enabling SPV nodes to ascertain the network's acceptance of the transaction without the need for storing the entire transaction history.
To authenticate a transaction, an SPV node utilizes a Merkle branch. This branch is a path of hashes in the Merkle Tree that proves a transaction's inclusion in a specific block. It includes the hash of the transaction itself, and the hashes of other transaction pairs up to the Merkle root. SPV nodes can verify this proof by iteratively hashing it until they obtain the block's Merkle root, which can be checked against the Merkle root in the block header.
By repeatedly hashing the Merkle branch, SPV nodes ensure the integrity of the transaction and its connection to the block. While SPV nodes cannot independently verify transactions, they can confidently confirm the network node's acceptance of a transaction by tracing its Merkle branch to a specific location in the chain. As subsequent blocks are added to the blockchain, further validation is achieved, reinforcing the network's acceptance of the transaction.
While SPV brings notable efficiency benefits, it is essential to acknowledge the trade-offs associated with this approach. SPV nodes, relying on network nodes for verification, become more vulnerable if the network is compromised. In such scenarios, malicious actors can exploit this vulnerability by generating fraudulent transactions that may be unwittingly accepted by SPV nodes. Moreover, SPV nodes may have limitations in detecting certain types of attacks due to their limited access to the full transaction history.
However, SPV nodes, while contributing to efficiency, are susceptible to various attacks that can undermine their security and integrity. Eclipse attacks involve isolating an SPV node by controlling its connections to legitimate network nodes, leading to false or manipulated information being presented to the targeted node. Sybil attacks, on the other hand, involve creating multiple fake identities to overwhelm an SPV node with conflicting information, potentially tricking it into accepting invalid transactions. Double-spend attacks exploit the lack of transaction history visibility in SPV nodes, allowing attackers to spend the same bitcoins more than once. Lastly, denial-of-service attacks aim to overload SPV nodes with a high volume of requests, impeding their normal functioning.
Bitcoin's design aims to strike a balance between efficiency and security. Full nodes ensure high levels of security but require more resources, while SPV nodes contribute to transaction verification efficiency. This delicate balance supports the overall robustness and functionality of the Bitcoin network.
It's important to note that within the SPV realm, different implementations exist. These implementations, such as Bloom filters, Neutrino filters, Electrum servers, and BIP 157/158, have varying characteristics in terms of privacy, bandwidth, scalability, and compatibility. These different approaches cater to diverse needs within the Bitcoin ecosystem.
The interplay between full nodes and SPV nodes is critical to achieving a balance of efficiency, scalability, and security within the network. SPV serves as a pragmatic compromise, optimizing the utilization of node resources while leveraging the security provided by full nodes.
Understanding SPV elucidates how the Bitcoin network accommodates lightweight nodes and verifies transactions efficiently. This feature enhances the accessibility and usability of Bitcoin while maintaining its fundamental principles.
Combining and Splitting Value
The ninth section of the Bitcoin whitepaper explains how the Bitcoin network efficiently manages transaction values. To illustrate, consider how efficiency, scalability, reduced transaction costs, and reduced complexity for users – all fundamental aspects of the Bitcoin protocol – find their embodiment in the process of combining and splitting transaction values.
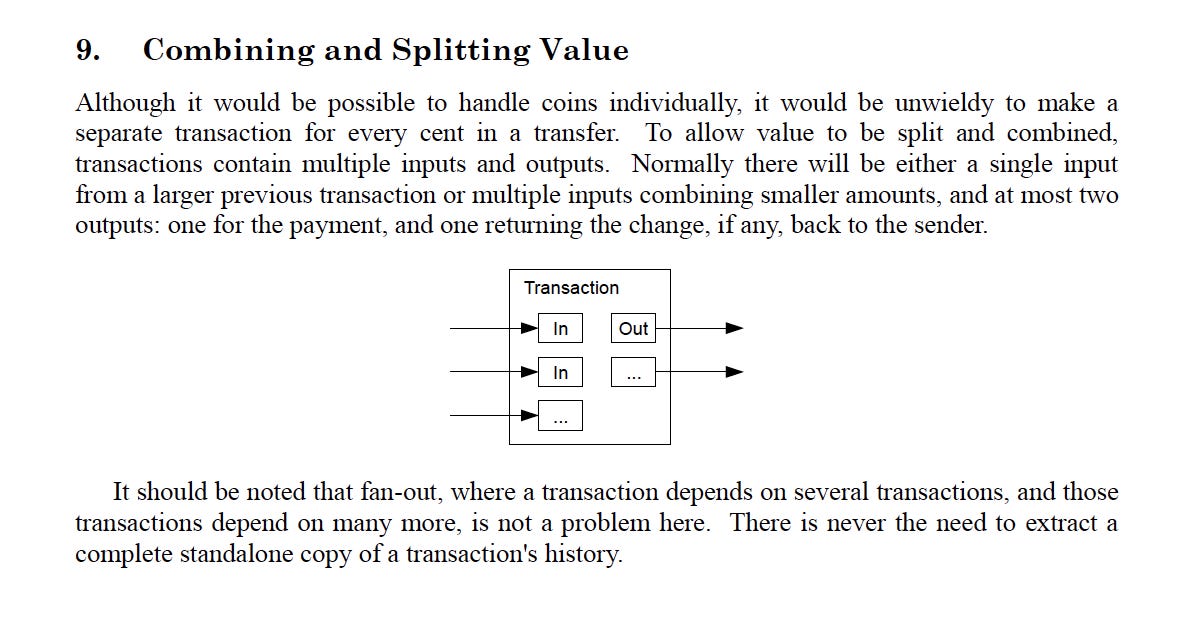
Transactions on the Bitcoin network can have multiple inputs and outputs, allowing for a flexible mechanism for combining and splitting value. For example, a transaction could involve sending bitcoins to multiple recipients or receiving bitcoins from multiple sources. This flexibility allows for the consolidation of value from various transactions into a single transaction, streamlining the transaction process and reducing the overall number of transactions on the network.
When constructing a transaction, inputs usually come from UTXOs, and there are typically two outputs: one for the payment and the other for returning any change back to the sender. The change output is calculated by subtracting the payment amount and the transaction fee from the total input value. This way, the inputs are spent entirely and any excess value is returned to the sender as a new output. The change output is assigned to the sender's address, completing the transaction.
The mechanism of combining and splitting value in transactions exemplifies a fundamental characteristic of the Bitcoin network's design. It aims to optimize the utilization of the blockchain, reduce transaction costs, and provide flexibility in managing transaction values. By consolidating multiple inputs and outputs, Bitcoin transactions become more streamlined and efficient, contributing to the scalability and overall functionality of the network.
In the broader context of Bitcoin's design, this approach involves trade-offs between efficiency and security. While combining and splitting value improves efficiency and reduces transaction complexity, it's important to ensure that the integrity and security of the network are not compromised. Bitcoin's design principles aim to strike a delicate balance between these factors, creating a robust and decentralized system for value transfer.
Understanding Unspent Transaction Outputs (UTXOs) in the Bitcoin System
🤔 What is a UTXO? 🧐
A UTXO, or Unspent Transaction Output, is a foundational concept in the Bitcoin system that determines the maximum amount of bitcoin that can be spent from a particular output. To grasp its significance more accurately, think of a UTXO as a digital IOU or check, representing the promise that the owner of a specific private key can claim a certain amount of bitcoins by creating a valid transaction.
In layman's terms: A UTXO is like a promise that you can get some bitcoins if you have the right password. It tells you how many bitcoins you can get, and who gave them to you. You can use UTXOs to pay other people with bitcoins.
💡 How Does it Work? 💭
In the Bitcoin network, every transaction generates new UTXOs, each linked to its specific transaction ID and output index, referencing the previous transaction that created it. When a user wants to send bitcoins to another party, they use one or more UTXOs as inputs to create a transaction. This transaction includes one or more outputs: one for the recipient, and one or more for the sender, which is commonly referred to as change.
In layman's terms: Every time someone pays with bitcoins, they make new UTXOs. Each UTXO has a number and a name that shows where it came from. When you want to pay someone with bitcoins, you use some of your UTXOs as payment. You also make new UTXOs for yourself and the person you are paying.
🛑 Unspent = Valuable 📈
The term “Unspent” in UTXO is what makes it so pivotal. Once a UTXO is spent, it is marked as invalid or spent by the network and cannot be used as an input in future transactions. This prevention of double-spending ensures the integrity and scarcity of bitcoins within the Bitcoin system.
In layman's terms: The word “Unspent” in UTXO means that you haven’t used it yet. Once you use a UTXO, you can’t use it again. This makes sure that no one can cheat and spend the same bitcoins twice. This also makes bitcoins rare and valuable.
🔗 A Transactional Ledger ⛓️
UTXOs, as individual IOUs, collectively form a transactional ledger on the blockchain. Each UTXO’s history can be traced back to its creation, providing transparency and security. However, it’s important to note that UTXOs do not directly form a chain of ownership; rather, they are linked to their originating transactions.
In layman's terms: UTXOs are like receipts that show who paid who with bitcoins. They are all stored on a big list called the blockchain that everyone can see. You can follow the history of each UTXO back to when it was created. This makes everything clear and safe.
🔒 Security and Consensus 🤝
The UTXO model plays a vital role in the security and consensus mechanisms of Bitcoin. Nodes on the network verify transactions by ensuring that referenced UTXOs are valid and unspent. This verification process maintains the integrity of the network and upholds the rules of the Bitcoin protocol.
In layman's terms: The UTXO system helps keep Bitcoin secure and fair. There are many computers on the network that check every payment with UTXOs. They make sure that the UTXOs are real and not used before. They also agree on the rules of Bitcoin and follow them.
⏳ Evolving UTXOs 🔄
As bitcoins are spent, UTXOs are updated accordingly. They are not physical or digital objects but rather data structures stored on the blockchain. UTXOs do not disappear entirely when spent but are marked as spent and excluded from the UTXO set, which comprises all valid and unspent UTXOs at any given time.
In layman's terms: As people pay with bitcoins, UTXOs change all the time. They are not things that you can touch or see, but just information on the blockchain. When a UTXO is used, it is marked as used and removed from the list of available UTXOs.
💡 Unlocking the Bitcoin System 💭
Understanding UTXOs unlocks the true workings of the Bitcoin system. Recognizing them as IOUs rather than physical coins or tokens emphasizes their dynamic nature. The UTXO model fosters secure transactions, preserves the decentralization of the Bitcoin network, and ensures the scarcity of this revolutionary digital currency.
In layman's terms: UTXOs are very important for how Bitcoin works. They show how each bitcoin is unique and traceable, and how people can pay each other securely and without anyone in charge. They also show how bitcoins are limited and scarce.
🧠 Embracing Complexity 🚀
Grasping the intricacies of UTXOs might seem challenging, but embracing this complexity is essential to comprehend the innovative architecture behind Bitcoin. Acknowledging the accuracy of UTXO definitions and their role in the Bitcoin ecosystem leads to a more comprehensive understanding of its decentralized and transparent financial framework.
In layman's terms: UTXOs might seem hard to understand at first, but learning more about them can help you appreciate how amazing Bitcoin is. Knowing what UTXOs are and how they work can help you understand Bitcoin’s design and goals better.
Privacy
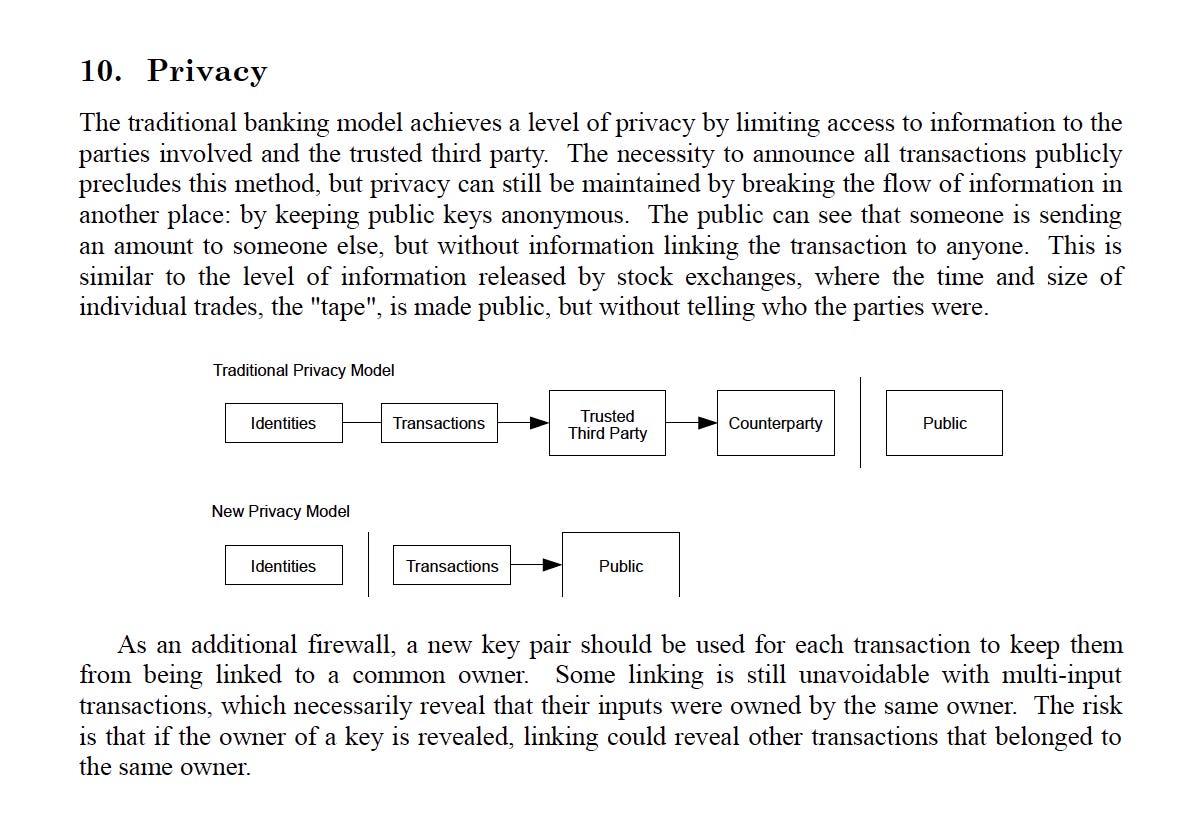
This section delves into how the Bitcoin network balances privacy with transaction transparency. Unlike the traditional banking model, where privacy is maintained by restricting information access to involved parties and a trusted third party, Bitcoin takes a distinct approach to privacy. It maintains the anonymity of public keys as the foundation for preserving privacy. Consequently, while transaction details are openly accessible, the identities of the parties involved remain undisclosed due to the use of multiple public keys. This system offers a level of privacy that, thanks to Bitcoin's innovative design, is comparable to or even superior to traditional banking systems.
In the Bitcoin ecosystem, public keys play a vital role in ensuring privacy. They are used to verify digital signatures that show the ownership of bitcoins in transactions. Furthermore, addresses are derived from public keys using one-way hash functions, which allow for a more convenient and concise representation. Importantly, these addresses serve as pseudonyms, safeguarding against the direct revelation of user identities unless correlated with additional information.
One technique that Bitcoin users can employ to enhance privacy is the use of multiple public keys. Users can generate a new pair of public and private keys for each transaction, and use them to create new addresses for receiving payments. This practice avoids the linkage of transactions to a single address or public key, mitigating the risk of compromising privacy. With Bitcoin, individuals have the power to protect their financial autonomy and privacy by taking advantage of its innovative features.
While Bitcoin offers a robust level of privacy, it is important to be aware of its limitations and challenges compared to traditional banking systems. The transparency of transaction details on the blockchain, though pseudonymous, presents a double-edged sword. While it offers privacy and anonymity desired by users, it can also introduce complexities in terms of transaction tracking and verification, given the absence of identifying information. Nevertheless, the Bitcoin community continuously explores and develops new technologies and methods to further enhance privacy within the network.
Considering transaction fees and user experience, the use of pseudonymous addresses does not have a direct negative impact. Instead, it provides users with the power to control and manage their financial interactions. Furthermore, additional privacy-enhancing technologies, such as mixing or CoinJoin, can be voluntarily adopted by users to further enhance privacy. The Bitcoin network enables individuals to protect their privacy while participating in a decentralized and censorship-resistant financial system.
The utilization of pseudonymous addresses stands as a fundamental feature of the Bitcoin network, contributing to its robust privacy infrastructure. While it successfully adds a layer of privacy and anonymity, it is crucial to recognize the potential trade-offs and the need for supplementary measures to enhance privacy and security. Bitcoin's design prioritizes the principles of decentralization, censorship resistance, and individual sovereignty, making privacy a key pillar of its system. By embracing and advancing the privacy features of Bitcoin, users can fully exercise their financial autonomy in a world that is increasingly reliant on digital transactions.
CoinJoin: Elevating Bitcoin Privacy and Security
🔍 What is CoinJoin or Coin Mixing?
CoinJoin, also known as Coin Mixing, is a privacy-enhancing technique used in Bitcoin. It aims to increase the anonymity of transactions by combining multiple payments from different users into a single transaction. This process makes it challenging to determine which user sent which payment, providing increased privacy and fungibility to the involved coins.
🔒 How Does CoinJoin Work?
Imagine a group of users who want to make transactions without revealing their individual payment details. In a CoinJoin transaction, these users collaborate and combine their payments into one large transaction, mixing them together. As a result, the transaction appears as a single entity, hiding the original source of each payment.
💡 Key Features and Benefits
1 · Privacy Enhancement: By obscuring the connection between inputs and outputs, CoinJoin breaks the trail of transactions, making it harder for third parties to trace the flow of Bitcoin.
2 - Fungibility: CoinJoin promotes the fungibility of Bitcoin, ensuring that each unit of the cryptocurrency is interchangeable and of equal value. With CoinJoin, coins with a common history are indistinguishable, enhancing their fungibility.
3 - Decentralization: CoinJoin can be facilitated by various methods and services, often implemented in decentralized wallets or services, contributing to the overall decentralization of the Bitcoin ecosystem.
4 - Automatic Transaction Execution: CoinJoin transactions are typically performed automatically by dedicated services like Wasabi Wallet or JoinMarket. These services efficiently execute the CoinJoin process, enhancing user convenience and adoption.
5 - Compatibility with Bitcoin Protocol: CoinJoin transactions are compatible with the existing Bitcoin protocol and do not require any changes to the network rules. Users can seamlessly participate in CoinJoin without altering the fundamental structure of the Bitcoin network.
🔄 The CoinJoin Process
1 - Gathering Participants: Bitcoin users interested in increasing their transaction privacy come together to form a CoinJoin transaction.
2 - Creating the Transaction: The participants share their Bitcoin transaction details with each other through a secure communication channel or a dedicated CoinJoin service.
3 - Mixing and Combining: The participants' Bitcoin transactions are combined into a single transaction, mixing the inputs and outputs in a way that obscures their original sources.
4 - Signing and Broadcasting: The combined Bitcoin transaction is signed by all participants, ensuring its validity, and then broadcasted to the Bitcoin network for confirmation.
🛡️ Limitations and Considerations
· Timing Attacks: While the CoinJoin system significantly enhances privacy, it's essential to consider that sophisticated adversaries could still attempt timing attacks to correlate transactions based on their timestamps. However, some CoinJoin services implement additional techniques such as variable input and output amounts, delayed broadcasting, or Chaumian blind signatures to further mitigate the risk of timing analysis.
· Transaction Size: CoinJoin transactions tend to be larger than regular transactions due to the involvement of multiple inputs and outputs, potentially incurring higher fees. However, some CoinJoin services employ optimization techniques like Schnorr signatures or SegWit to reduce the transaction size and associated fees.
Calculations
The calculations section of the Bitcoin white paper is one of the most important and fascinating parts of the document, as it provides a mathematical framework for understanding the security and scalability of the network. One of the primary challenges the calculations address is preventing double-spending—a scenario where someone attempts to spend the same bitcoins more than once. The calculations explain how the network prevents double-spending by using a proof-of-work system, which is like a puzzle that miners have to solve to create new blocks and confirm transactions. The calculations also explain the network's use of a consensus rule—everyone agrees to follow the longest chain of blocks, signifying the most proof-of-work.
The calculations show how hard it is for an attacker to double-spend by creating a different chain of blocks that contains a different version of their transaction. The attacker would have to catch up with the honest chain, which is constantly growing as more blocks are added by honest miners. The calculations estimate the probability of the attacker catching up, based on how much computing power they have compared to the honest miners, and how many blocks have been added to the honest chain since the transaction was confirmed. To illustrate this, let's use an example from the white paper. Suppose an attacker has 10% of the network's computing power, and they want to double-spend a transaction that has been confirmed in one block. The probability that they can catch up with the honest chain after one block is 0.1 (10%). However, if they wait for six blocks to be added to the honest chain, the probability drops to 0.0001 (0.01%). This means that it is very unlikely that they can succeed in double-spending, even if they have a lot of computing power.
The calculations also suggest how long a recipient of a transaction should wait before being confident that the transaction cannot be reversed by the attacker. The longer they wait, the more blocks are added to the honest chain, and the harder it is for the attacker to catch up. The calculations give an example of waiting for six blocks, which takes about an hour on average, and show that the probability of the attacker catching up is very low, even if they have a lot of computing power. This means that waiting for six confirmations is usually enough to ensure that a transaction is secure and irreversible. However, depending on the value and importance of the transaction, the recipient may choose to wait for more or fewer confirmations as they see fit.
The calculations section of the white paper builds on the previous sections, where Satoshi Nakamoto introduced the concept and design of Bitcoin as a peer-to-peer electronic cash system that does not rely on trusted third parties or intermediaries. The calculations section also relates to other sections, where Satoshi Nakamoto discusses some practical aspects and implications of Bitcoin, such as its privacy features, its network topology, and its future improvements. The calculations section explains how these aspects and implications are done with calculations using a clever combination of cryptography, game theory, and network effects. The calculations section also shows how Bitcoin can adapt to new developments and changes in the network by using various solutions and conducting further research.
In my view, the calculations segment of the white paper underscores the elegance and innovation of Bitcoin's design in a powerful way. It illuminates how Bitcoin ingeniously solves multifaceted challenges with straightforward and sophisticated mathematical approaches. Moreover, it highlights the equilibrium that Bitcoin strikes between security and scalability, often necessitating intricate trade-offs and decisions. Furthermore, it demonstrates Bitcoin's dynamism and adaptability, with the network continually seeking solutions and conducting research. These elements, I believe, help to articulate why Bitcoin stands as such a groundbreaking and revolutionary invention.
Conclusion of the whitepaper
In the concluding section of the Bitcoin whitepaper, Satoshi Nakamoto succinctly encapsulates the paper's central tenets. The conclusion offers a crisp restatement of the key problem Bitcoin was designed to solve: the issue of double-spending in digital transactions. It also presents a contrast to traditional transaction models, which often rely heavily on trust-based third-party systems and expose users to potential vulnerabilities and inefficiencies.
Through its innovative peer-to-peer structure and proof-of-work consensus mechanism, Bitcoin presents a promising alternative. It creates a public, tamper-resistant transaction record that becomes computationally demanding to alter, especially when the majority of CPU power resides with honest nodes. This resilience is further bolstered by the system's inherent simplicity, with nodes operating in unison but requiring minimal coordination.
The conclusion also underscores the adaptability of the Bitcoin network. It speaks to the system's flexibility, with nodes free to join and depart at will, yet seamlessly reintegrating upon return by accepting the proof-of-work chain as the record of events during their absence. This consensus mechanism facilitates the enforcement of necessary rules and incentives, fostering a shared understanding and cooperation within the network.
Nakamoto concludes by indicating the transformative potential of Bitcoin, emphasizing that while challenges exist, the proposed system provides a trustless solution that doesn't compromise on security or efficiency. This conclusion effectively integrates the key proposals and arguments presented throughout the paper, underscoring the necessity for a decentralized, secure network and the pivotal role of proof-of-work in maintaining an immutable transaction history.
Lastly, the conclusion accentuates the principles underpinning the Bitcoin concept. It calls out the limitations of traditional banking and financial systems and puts forth Bitcoin as a solution capable of offering irreversible transactions and enhanced privacy—an attribute that conventional financial institutions often struggle to provide.
References section
The Bitcoin whitepaper's reference section provides a snapshot of the wide range of intellectual influences that have shaped the development of Bitcoin. The list encompasses a diverse range of materials that underline Satoshi’s extensive research in fields like distributed systems, cryptography, and computer science.
W. Dai's "b-money" (1998) proposed an anonymous, distributed electronic cash system using proof-of-work to prevent double-spending, providing inspiration for Bitcoin's architecture.
Massias, Avila, and Quisquater's work on a secure timestamping service (1999) highlights the importance of maintaining a secure and tamper-evident record of transactions.
The works of Haber, Stornetta, and Bayer in 1991 and 1993 focus on the efficiency, reliability, and security of digital timestamping. Their 1993 paper, "Improving the efficiency and reliability of digital time-stamping," co-authored by D. Bayer, has had a substantial influence on the method Bitcoin uses for the same. Haber and Stornetta also continued their exploration into secure timestamping with "Secure names for bit-strings" in 1997.
A. Back's "Hashcash" (2002) introduced a proof-of-work system to combat spam, an approach that Bitcoin adapted and integrated.
R.C. Merkle's work on public key cryptosystems (1980) presented the Merkle tree structure, a critical component of the Bitcoin protocol.
W. Feller's "An introduction to probability theory and its applications" (1957) provided the mathematical basis for probability calculations within the Bitcoin system.
These cited works, including academic papers, a book, and even a web-based text, indicate a broad scope of research. These sources have undergone rigorous peer reviews or have stood the test of time, underpinning the academic robustness of the Bitcoin whitepaper.
While these references provide inspiration and foundational concepts, the whitepaper's true accomplishment lies in its synthesis of these disparate ideas into a cohesive, novel system that is Bitcoin. By drawing on and integrating these sources, the author demonstrates a unique capacity for innovation in the field of digital currency.
Final Thoughts
The Bitcoin whitepaper, authored by the pseudonymous Satoshi Nakamoto, puts forth a revolutionary decentralized cryptocurrency system, Bitcoin, that operates autonomously from centralized control and intermediaries. This deep-dive analysis of the whitepaper unraveled Bitcoin's foundational elements, including digital signatures, proof-of-work mechanism, and the peer-to-peer network architecture, illuminating its inherent strengths like resistance to censorship and identifying potential limitations such as scalability issues and certain security vulnerabilities.
The whitepaper is more than a static blueprint. Rather, it provides an adaptable framework for the future, suggesting that Bitcoin's evolution will align with advancements in cryptography, distributed systems, and peer-to-peer networking. Emerging technology could reveal new applications and use cases for Bitcoin, further demonstrating its transformative potential.
The persistent impact of the whitepaper lies in its bold vision of a decentralized, transparent, and peer-to-peer financial system, which continues to guide Bitcoin's evolution. While it doesn't lay out a definitive trajectory, it leaves room for the system to scale and evolve, keeping pace with technological advancements, and potentially revolutionizing our financial ecosystem.
The whitepaper stands as a fundamental document that goes beyond detailing a novel cryptocurrency. It embodies the spirit of innovation and the quest for financial freedom and privacy, principles that continue to guide the journey of Bitcoin and the broader cryptocurrency landscape. As we continue to push the boundaries of this technology, the whitepaper's tenets will persist as a guiding light, steering the future of cryptocurrency innovation.
Until next time, stay curious my friends!
INTERLINKED IDEAS
If you arrived here first and found yourself eager to deepen your understanding of Bitcoin? I invite you to deep-dive into a comprehensive journey from the basics to advanced concepts of Bitcoin. Here, you'll find everything you need to begin learning to navigate Bitcoin's dynamic world confidently.
Unraveling the Bitcoin Phenomenon: Book Recommendations for an In-Depth Understanding
To accompany our in-depth analysis of the Bitcoin whitepaper, here are a few recommended readings for those interested in delving deeper into the world of Bitcoin and blockchain. These books were selected to complement the themes explored in the essay. The aim is to deepen your understanding of the world of cryptocurrencies and provide valuable insights into this transformative technology. As always, transparency is crucial—I maintain my editorial authority, while AI aids in the curation.
"Mastering Bitcoin: Unlocking Digital Cryptocurrencies" by Andreas M. Antonopoulos: Antonopoulos provides a detailed guide to understanding the mechanisms behind Bitcoin. It complements our technical dissection of the Bitcoin whitepaper.
"The Book of Satoshi: The Collected Writings of Bitcoin Creator Satoshi Nakamoto" by Phil Champagne: This book collects the various writings of Satoshi Nakamoto, providing a deeper insight into the mind of Bitcoin's enigmatic creator.
"The Internet of Money" by Andreas M. Antonopoulos: In this book, Antonopoulos presents a series of essays offering philosophical reflections on the implications of cryptocurrencies and their potential to revolutionize our understanding of money and finance. It resonates with our essay's exploration of the broader implications of the Bitcoin whitepaper.
"The Bitcoin Standard: The Decentralized Alternative to Central Banking" by Saifedean Ammous: Ammous takes readers through the historical context of Bitcoin, exploring the economic, philosophical, and technological principles that underpin it. The book offers a solid understanding of Bitcoin's role as a decentralized alternative to traditional banking, complementing the discussions in our essay.
"Layered Money: From Gold and Dollars to Bitcoin and Central Bank Digital Currencies" by Nik Bhatia: Bhatia presents a comprehensive exploration of the evolution of money, from gold to Bitcoin. The book's nuanced examination of Bitcoin within the larger historical and economic context of monetary systems will deepen readers' appreciation for the innovation introduced by the Bitcoin whitepaper.